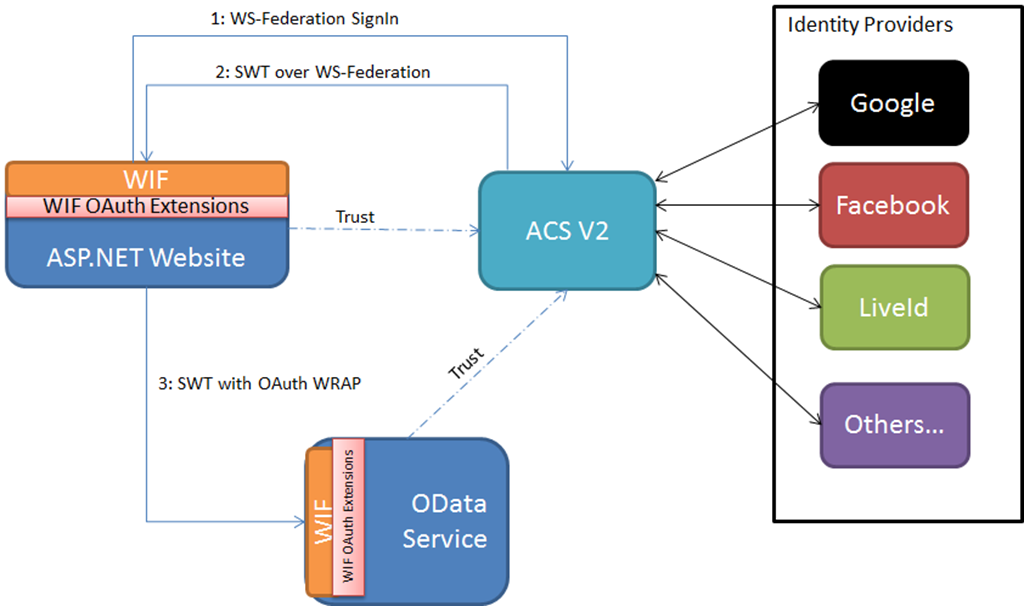
In this post I’ll walk you through the steps of exposing a ‘Windows Server AppFabric’ hosted workflow service over the Azure service bus. IIS/AppFabric hosted services are message activated so they cannot be visible on the servicebus until they are activated. So in this post, I’ll use the AutoStart feature of AppFabric to make my service available over service bus.
Create a workflow service project using Visual Studio
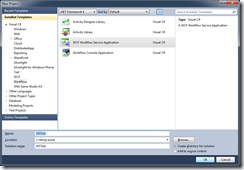
VS would generate a .xamlx based service and a default web.config file

The generated web.config uses the new WCF 4.0 default configuration option so no <service> tag was generated. If you run the service now, default endpoints would automatically be generated based on the base address of the service provided by the IIS.
Service bus endpoints requires an address in the service bus namespace so I can’t use IIS provided base address which means I can’t use the default endpoints feature. So the first set of changes would to be revert back to the old-style explicit endpoint definition.
<services>
<service name="Service1">
<endpoint address="http://eval01.servicebus.windows.net/wfappfabric/" binding="ws2007HttpRelayBinding" contract="IService"/>
<endpoint address="http://eval01.servicebus.windows.net/wfappfabric/mex" binding="ws2007HttpRelayBinding" kind="mexEndpoint"/>
</service>
</services>
The service name & contract name (‘Service1’ & ‘IService’) can be found from the properties of the workflow and the receive activity respectively. Because I’m using an absolute address for my endpoint, WCF tells me to disable the multipleSiteBindings by removing the following element.
<serviceHostingEnvironment multipleSiteBindingsEnabled="true" />
Next I’ll change the default ws2007HttpRelayBinding to disable security.
<bindings>
<ws2007HttpRelayBinding>
<binding>
<security mode="None" relayClientAuthenticationType="None" />
</binding>
</ws2007HttpRelayBinding>
</bindings>
Configure the ACS security for the ServiceBus and specify the discovery mode to public so that I can see my service in the registry. All of this is done using a default a endpoint behavior.
<endpointBehaviors>
<behavior>
<serviceRegistrySettings discoveryMode="Public" />
<transportClientEndpointBehavior credentialType="SharedSecret">
<clientCredentials>
<sharedSecret issuerName="owner" issuerSecret="SECRET=" />
</clientCredentials>
</transportClientEndpointBehavior>
</behavior>
</endpointBehaviors>
Using the project properties, I’ll configure the service to run under IIS/AppFabric

I can now see my endpoints in the AppFabric management console but I can’t see my service in the Service Bus registry because it’s not activated yet.

So I need to configure Auto-Start feature on this service which I can easily do using the AppFabric management console.
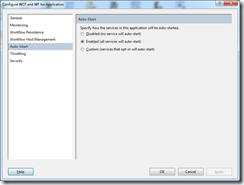
After configuring AutoStart I can straight a way see my service in the registry

When I browse to my service I see the standard help page which the metadata URL

Download: Web.config
 Email
Email Twitter
Twitter LinkedIn
LinkedIn