First of all my apologies for not doing a good job here. I always planned to contribute this to the excellent identity server but I never got enough bandwidth to do so. I’m constantly receiving request to share the details here so I decided to share notes/steps required to enable this and hopefully someone from community would do the bits I have long promised.
Here are steps…
- Create a basic STS or tweak & use the lovely thinktecture IdentityServer v2 (my recommendation)
- Within identity server, add a Relying Party Trust to ‘urn:federation:MicrosoftOnline’ which is the unique identifier used by of Azure AD for federation.
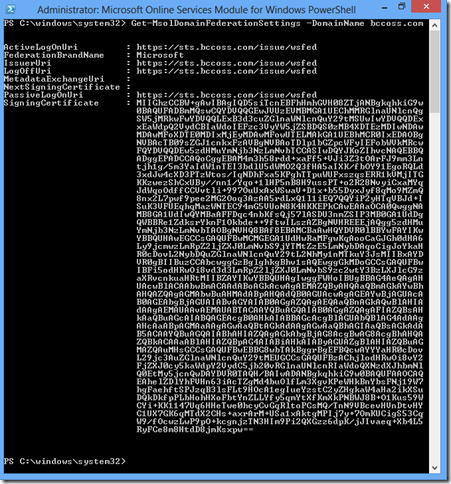
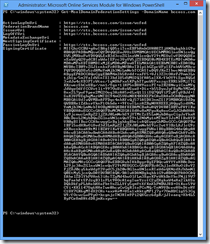
- Establish a trust relationship between identity server and Azure AD using the Set-MsolDomainAuthentication cmdlet. This is how my trust relationship look like:
4. The IssuerUri MUST match the issuer URI of SAML assertion.
5. The protocol MSUT be WS-Federation for browser-based SSO
6. Following claims MUST be included in the issued tokens
- http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID
- http://schemas.xmlsoap.org/claims/UPN
7. The UPN must also be set as a name identifier.
Identity server code change # 1
var nameid = new Claim(ClaimTypes.NameIdentifier, “7960192”);
nameid.Properties[ClaimProperties.SamlNameIdentifierFormat] = “urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified”;
var outputClaims = new List<Claim> {
new Claim(“http://schemas.microsoft.com/LiveID/Federation/2008/05/ImmutableID”,”7960192″),
new Claim(“http://schemas.xmlsoap.org/claims/UPN”, “zulfiqar@bccoss.com”),
nameid
};
8. The signing algorithm MUST be SHA-1. Signing certificate can be a self-signed SSL certificate.
Identity server code change # 2
scope.SigningCredentials = new X509SigningCredentials(signingCert, SecurityAlgorithms.RsaSha1Signature, SecurityAlgorithms.Sha1Digest);
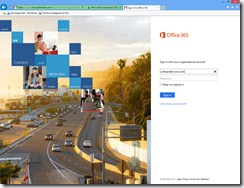
9. The token MUST be sent to: https://login.microsoftonline.com/login.srf
Looking forward to see this in identity server soon…
 Email
Email Twitter
Twitter LinkedIn
LinkedIn